Passwords are like the cockroaches of the internet. They really, despite all of our best efforts, are very hard to kill off. And companies have been trying to do it for years. The average office worker in the United States must keep track of between 20 to 40 different username and password combinations. With so many passwords to remember, it’s no wonder why many of us use the same ones over and over or have a running list of passwords saved somewhere on our computers, phones or notebooks.
Passwords are a very serious and expensive security risk. It’s why companies like Microsoft, Apple, and Google are trying to reduce our dependence on them. But the question is, can these companies break our bad habits? Passwords, by themselves, are just not that secure. In a 2015 interview with John Oliver, Edward Snowden explained just how easy it is to crack a typical password. Bad passwords are one of the easiest ways to compromise a system. For somebody who has a very common eight-character password, it can literally take less than a second for a computer to go through the possibilities and pull that password out.

I think we’re going to have a no passwords future because it just gets rid of a lot of problems. You never know when the bad guy has your password, at the end of the day. – Kevin Mitnick
He’s pretty well known in the hacker community.
I started off many, many years ago as a black hat hacker. I wasn’t hacking to cause harm or to make money. It was all about the intellectual challenge, curiosity and seduction of adventure. And then I pushed the envelope, and I pushed it so far, I became the world’s most wanted hacker. And I was pursued by
federal law enforcement agencies. And they eventually caught up with me and I ended up serving five years in federal prison. – Kevin Mitnick

Nowadays, he’s an ethical hacker, assisting companies to identify their security vulnerabilities and helping to fix them. And finding your usernames and passwords, it’s much easier than you might think.
There’s a site out there called weleakinfo.com. So what weleakinfo is, it’s a site that has aggregated a bunch of data breaches. And so what happens is the data, namely your username and passwords that are on these data breaches, get aggregated because they’re publicly available. And there’s sites like weleakinfo, make it like a Google, where you can actually just put in an email address of yourself or a friend, and all the prior data breaches that contained your username or your email address, it actually reveals the password. All it takes to find the site is a quick Google search, and users can get access to more than 10,000 data breaches for as low as $2.
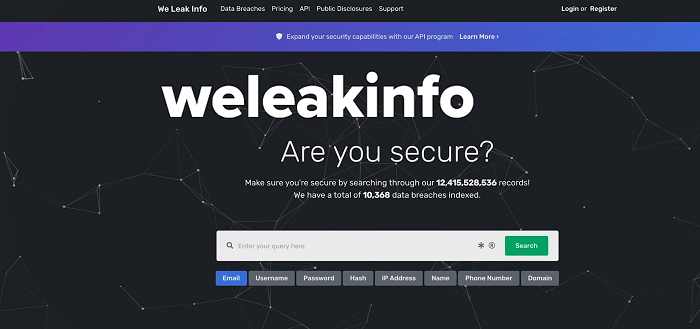
And it’s not even the only website to offer these services. Simply put, passwords are not fit for purpose for today’s networked economy. They present challenges to consumers in the sense that they’re either hard to remember or they’re too easy to remember, in which case are easier to mimic and steal. For businesses, they represent a huge liability, in the sense that the vast majority of data breaches are caused by passwords, either passwords that slip from an employee and expose a database or allows other bad actors to get into their systems.
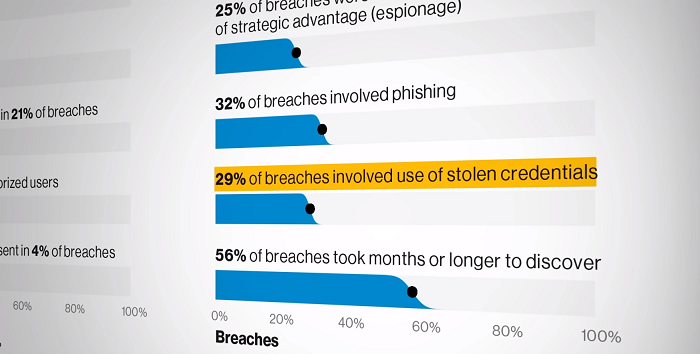
So passwords present challenges across the board. A report that looked at 2,013 confirmed data breaches found that 29 percent of those breaches involved the use of stolen credentials. In another study, researchers found that the average cost of a data breach in the U.S. was more than $8 million. And even when passwords are not stolen, companies can lose a lot of money resetting them. Our research has shown that the average fully-loaded cost of a help desk call to reset a password is anywhere between $40 or $50 per call.
Generally speaking, a typical employee contacts a help desk about somewhere between six and ten times a year on password-related issues. So if you just do the simple multiplication of six to ten times $50 per call, times the number of employees in your organization, you’re talking significantly hundreds of thousands of dollars or even potentially millions of dollars a year. And that’s just really the IT operations costs, that’s not really factoring necessarily the productivity cost that gets lost by the user having to wait for maybe 20 minutes, 30 minutes or even longer to actually have the password issue resolved to their satisfaction.

In large companies like Microsoft, Apple and Google with upwards of 100,000 employees each, these costs can quickly add up. A former Microsoft executive told CNN in 2018, that the company spends more than $2 million dollars each month in help desk calls, helping people to change their passwords. With the details of our personal and professional lives increasingly residing in the digital realm, those costs are likely to grow. The first use of the computer password dates back to the early 1960s at MIT.
At the time, computers were these huge contraptions that could only manage the work of one person at a time. This limitation frustrated Fernando Corbató, who came up with the computer time sharing system. CTSS was an operating system that distributed a computer’s processing power so that multiple people could
use it at once. This naturally led to the issue of privacy. So Corbató created the password. Ironically, the first computer to use passwords was also the first one to be hacked. One of the researchers in Corbató’s lab found that he needed more time to complete his work than the weekly hours allotted to him.
So he printed out all the passwords stored on the system and used them to log in as his colleagues. The conventional rules of password creation adopted by companies, federal agencies and universities were attributed to a document released by the National Institute of Standards and Technology in 2004. The documents suggested that users should have a minimum of eight-character passwords and that those passwords should include at least one uppercase letter, one lowercase letter, one number, and 1one special character, and be changed regularly.
But in 2017, NIST rewrote the password rules. This time, the agency suggested using long, easy to remember phrases instead of crazy characters and only changing your password if it might have been hacked. Passwords have come a long way since the 1960s.
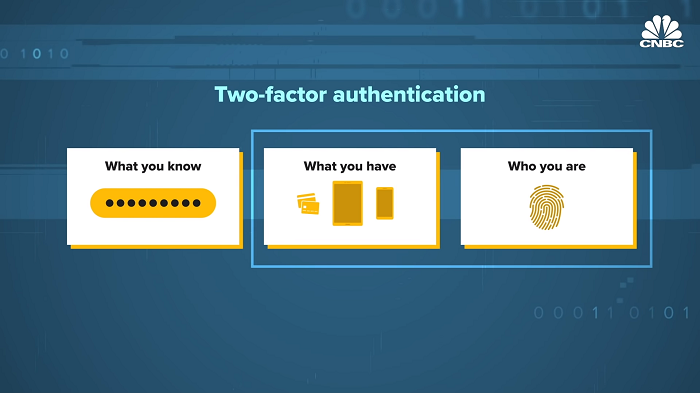
With innovations such as fingerprint readers and face scanning on smartphones, verifying your identity now often goes beyond just entering a password. This comes in the form of two-factor and two-step authentication. There’s three forms of authentication. One is what you know, such as a password or a pin. The second thing is what you have. So possession of a device in your hands. And a third means of authentication is who you are, like a biometric. The password alone is the highest risk way of authenticating. And that that leads to phishing and data breaches and all the nefarious things we see on the web today.
Any form of two-factor authentication is better than passwords alone. What I want to note, though, is that not all two-factor authentication is created equal. Things like getting SMS messages, so a text message with a pin code, is both inconvenient but also can be spoofed and is not a foolproof means of second-factor authentication. NIST even restricted the use of one-time passwords being sent over SMS as a means of two-factor authentication. For something to be two-factor versus two-step, the authentication elements must come from two separate categories.
An example of two-factor authentication is withdrawing money from an ATM. First, you insert your bank card, something that you possess. And then you were asked for a pin, something that, you know. Biometrics are the newest form of authentication and have risen in popularity thanks to smartphones that include fingerprint readers and face-scanning cameras. Meanwhile, digital assistants like Siri, Alexa, and Google Assistant have advanced voice recognition technologies.
In fact, a number of banks, including Chase and Barclays, now allow their customers to verify their identity using voice biometrics. When customers call in, their voice is automatically matched to a previously recorded voiceprint, that’s made up of more than 100 characteristics such as pitch, accent, and shape of your mouth.
One organization that’s been at the forefront of bringing two-factor authentication standards to the masses is the FIDO Alliance. The FIDO Alliance, which stands for, Fast Identity Online, is a consortium of more than 250 companies who are working together to reduce the industry’s reliance on passwords by
standardizing two-factor authentication. This past year, we’ve seen FIDO become a core part of the Android and Windows operating system, meaning that any Android 7 or later handset or any Windows 10 machine can leverage actual onboard biometrics for that device.

So a fingerprint reader, a face scanner, whatever it might be, to log in rather than using passwords. Other companies that work with the FIDO Alliance include eBay, Facebook, Twitter, PayPal and Bank of America. Even the U.S. government has adopted the standard. FIDO’s big advantage over other standards
comes down to where it stores users’ personal information. The core problem with passwords is that they reside on a server.
The problem with that is that when it sits on a server, they can be stolen by a hacker. Additionally, someone can impersonate you quite easily, either by phishing your credentials or by buying your credentials off the Dark Web and then trying to stuff them into the account. Everything FIDO does is local on the
device, which does a couple of things. One, it’s easier. But perhaps most important, it protects your privacy. So you can always change your password if it’s hacked. But you really can’t take your face back. You can’t take your fingerprint back. So it’s very important that companies that are using biometrics use local-match biometrics, meaning match-on-device, which is what FIDO supports to protect user privacy and have enhanced user experience.

Microsoft introduced Windows Hello to customers in 2015 with its devices running Windows 10. Windows Hello allowed users to ditch the password and log into their devices with just their face, fingerprint or pin. Like FIDO, Microsoft has said it stores user biometrics on the device instead of on a cloud. In 2018, Microsoft announced that it would support logging in to Windows 10 with FIDO2 compatible devices, such as hardware keys made by Yumiko.
Microsoft Authenticator is an app that allows users to take advantage of two-factor authentication on any device, not just those running Windows 10. Alex Simmons, Vice President of Microsoft’s identity division, said in a tweet that the company has more than 80 million unique monthly users that sign in with a passwordless method. Apple’s been encouraging the use of biometric authentication since it came out with Touch ID on the iPhone 5S back in 2013.
The company called Touch ID the gold standard for consumer device biometric protection until it introduced Face ID on the iPhone X in 2017. And the data for Touch ID has been 1 in 50,000, meaning that the chance that a random person could use their fingerprint to unlock your iPhone has been about 1 in 50,000 and it’s been great. So what are the similar statistics for Face ID? 1 in a 1,000,000. Back in 2016, Apple also introduced Auto Unlock, a feature for macOS.
In its guidelines to app developers, Apple stresses that apps should support biometric authentication whenever possible and that apps should only ask for a username and password as a fallback if the first method fails. Google has also been working to make passwords a thing of the past. The company has required its employees to use physical security keys since early 2017 and has seen a huge reduction in phishing. In August of 2018, the company released Titan to consumers.
Titan is a physical key that allows users to take advantage of two-factor authentication on their computers or smartphones. In 2019, Google announced that phones running Android 7 would all come with a built-in security key using Bluetooth. A few months later, Google extended that function to iOS devices, meaning that iPhone and iPad users could now use their secondary Android smartphones as a security key whenever logging into their Google accounts on an iOS device. While Microsoft’s Windows 10 devices and Google’s new Android devices are FIDO2 certified, Apple has been slower to adopt the standard in its products.
Even though Touch ID and Face ID made biometric authentication the norm for unlocking our phones, Apple’s devices are still not FIDO certified. But Apple is making strides. Of late, Apple’s been supporting FIDO technology both on iOS and on macOS. So the latest versions of their operating system support FIDO, meaning that if you’re accessing a website that supports FIDO on an Apple device, you’ll be able to leverage FIDO authentication as well.
The Department of Justice has also been moving away from password authentication. The agency adopted a single-sign-on method back in 2017. One of the reasons why passwords persist is that they are universal, they can be used by anyone. There are no limitations. There’s no special hardware requirements. You don’t have to have a certain kind of phone or a certain kind of laptop. Anyone can use passwords. There are a few key challenges to really moving beyond being dependent on passwords. One of them is technical, and that’s FIDO has been seeking to address. And we’ve now created the technical
standards that are web standards for authentication that does not depend on passwords.
Another challenge is behavioral. And we’ve been trained with this risky way of authenticating using passwords. We’ll have to be untrained to use simpler, but new mechanisms for logging in. So I think there’ll be some behavioral changes that need to take place, some education. You know, the good news is these changes are for the better and for the simpler. And so, we think that people will embrace these changes at the same time as new technologies roll to market to enable us collectively, on the whole, to move beyond passwords.
Experts say that getting rid of the password will be a long journey, especially when it comes to getting people to ditch their bad habits. The consumer approaches will be very much opt-in. In other words, if users actually want strong authentication, companies will be able to provide it to them, but just because it’s available, doesn’t mean that every customer is going to go for it. You may now need to start collecting information about the user like a mobile phone number that you need to use to communicate with them.
And perhaps users don’t want to provide that information or they’re reluctant to. On the consumer side, I believe passwords will be slower to get rid of. This also means that the risk of breaches of consumer sites will persist for the foreseeable future.
Great content! Super high-quality! Keep it up! 🙂
say thanks to a lot for your internet site it aids a lot.
It worked for me!! Thank you for the guide. Keep it up man.
I appreciate you helping me learn more about the topic.